UWB has a long history, but today’s use cases offer unique capabilities to deliver compelling new experiences. There are three primary categories of use cases that will help UWB become an essential technology for future connected devices.
Hands-Free Access Control
Secure access technologies are used to protect everything from high-security labs and corporate workspaces to private homes and garages. The traditional setup has a user perform an action – enter a code on a keypad, place a finger on a scanner, tap a badge, wristband or smart phone on a reader – to open a doorway and enter a secure area. With UWB, however, a user simply moves toward the door and it opens, or moves away from it and it locks. The UWB-based solution tracks a person’s approach, verifies security credentials, and lets the person pass without having to stop.
Location-Based Services
With location-based services, UWB brings positioning functionality with a high degree of accuracy to indoor environments, making it easier to navigate large spaces such as airports and shopping malls, as well as providing assistance in finding a car in a multi-story parking garage. Within a health care setting, UWB can be used for locating both patients and assets.
Device-to-Device Services
With device-to-device services, two UWB-enabled devices share relative ranging and positioning data to localize each other. This makes it possible for two people with mobile phones to locate each other with precision or transmit files by pointing their phones at one another. In smart homes, networked devices and appliances can respond to a person’s presence automatically. When somebody enters a room, the lights can turn on, the thermostat can be set to the preferred temperature, and a favorite playlist can begin streaming on an audio system.
THE UNIQUE PULSE SIGNAL OF ULTRA-WIDEBAND
An important feature of UWB is that the pulses resist a common difficulty, known as the multipath effect. This happens when radio signals reach the receiver by more than one path because of reflection and/or refraction caused by natural or manmade objects close to the main signal path. Immunity to the multipath effect increases positioning accuracy, especially when compared with alternative technologies that are more susceptible. Resistance to narrowband fading and jamming also helps to make UWB a very robust technology option, even when multiple UWB systems are used simultaneously.
PREVENTION OF RELAY ATTACKS
In the United Kingdom, the vehicle recovery company Tracker reports that, in 2019, 92 percent of all vehicles stolen and recovered were taken without using the owner’s keys. For automobile theft, one of the most common security failures is the “relay attack.” Car thieves have discovered that passive keyless entry systems, which use ranging technology to detect the approach of the driver, are vulnerable to relay attacks. So vulnerable, in fact, that relay attacks are now a preferred method for taking a car while it sits locked in a driveway.
The attack works by tricking the car into thinking the key and its owner are close by. The setup takes two people, each with a hacking device. The first stands close to the car and uses their device to relay signals from the car to the second thief. The second thief stands close to the house holding a device that transmits the relayed signal from the car into the house....
继续阅读完整内容
请查看下方广告以解锁文章剩余内容
Computerworld recently said that, “One way to think of it is as a radar that can continuously scan an entire room and precisely lock on to an object like a laser beam to discover its location and communicate data.”
UWB has a long history, but today’s use cases offer unique capabilities to deliver compelling new experiences. There are three primary categories of use cases that will help UWB become an essential technology for future connected devices.
Hands-Free Access Control
Secure access technologies are used to protect everything from high-security labs and corporate workspaces to private homes and garages. The traditional setup has a user perform an action – enter a code on a keypad, place a finger on a scanner, tap a badge, wristband or smart phone on a reader – to open a doorway and enter a secure area. With UWB, however, a user simply moves toward the door and it opens, or moves away from it and it locks. The UWB-based solution tracks a person’s approach, verifies security credentials, and lets the person pass without having to stop.
Location-Based Services
With location-based services, UWB brings positioning functionality with a high degree of accuracy to indoor environments, making it easier to navigate large spaces such as airports and shopping malls, as well as providing assistance in finding a car in a multi-story parking garage. Within a health care setting, UWB can be used for locating both patients and assets.
Device-to-Device Services
With device-to-device services, two UWB-enabled devices share relative ranging and positioning data to localize each other. This makes it possible for two people with mobile phones to locate each other with precision or transmit files by pointing their phones at one another. In smart homes, networked devices and appliances can respond to a person’s presence automatically. When somebody enters a room, the lights can turn on, the thermostat can be set to the preferred temperature, and a favorite playlist can begin streaming on an audio system.
THE UNIQUE PULSE SIGNAL OF ULTRA-WIDEBAND
An important feature of UWB is that the pulses resist a common difficulty, known as the multipath effect. This happens when radio signals reach the receiver by more than one path because of reflection and/or refraction caused by natural or manmade objects close to the main signal path. Immunity to the multipath effect increases positioning accuracy, especially when compared with alternative technologies that are more susceptible. Resistance to narrowband fading and jamming also helps to make UWB a very robust technology option, even when multiple UWB systems are used simultaneously.
PREVENTION OF RELAY ATTACKS
In the United Kingdom, the vehicle recovery company Tracker reports that, in 2019, 92 percent of all vehicles stolen and recovered were taken without using the owner’s keys. For automobile theft, one of the most common security failures is the “relay attack.” Car thieves have discovered that passive keyless entry systems, which use ranging technology to detect the approach of the driver, are vulnerable to relay attacks. So vulnerable, in fact, that relay attacks are now a preferred method for taking a car while it sits locked in a driveway.
The attack works by tricking the car into thinking the key and its owner are close by. The setup takes two people, each with a hacking device. The first stands close to the car and uses their device to relay signals from the car to the second thief. The second thief stands close to the house holding a device that transmits the relayed signal from the car into the house. The key, sitting somewhere inside the house, receives the signal from the car and responds as normal. The response is relayed back to the car, fooling the system into thinking the owner is close by and allowing entry into the vehicle. A second relay starts the ignition.
Relay attacks work because the current ranging technology used to measure the distance between the key and the car relies on signal strength. A weak signal means the key is far away and a strong signal means the key is close by. In a relay attack, the legitimate wireless signals used to unlock the door and start the car are intercepted and amplified, causing the door to open and the motor to start even though the key isn’t actually near the car.
With UWB technology, quick measurements are used to determine distance very precisely so the car doesn’t have to make assumptions. Any attempt to intercept and send the UWB signal, as in a relay attack, will only delay the arrival of the responding device’s acknowledgement signals, making it clear to the UWB-based lock and ignition that the responding device is actually farther away, not closer. With UWB, the car’s assumption is replaced with certainty, and that makes the passive keyless entry system much more secure.
UNDERSTANDING TIME OF FLIGHT
Based on the constant speed of light, the time of flight (ToF) calculation uses signal travel times to determine distance. Figure 1 gives a basic illustration of how the ToF calculation works between any two devices – such as a car and a key fob – equipped with UWB.
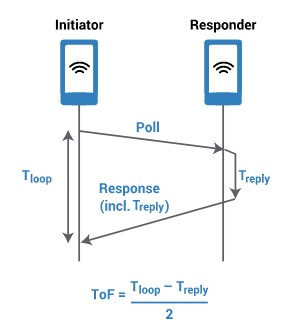
To calculate the ToF, we measure the round-trip time it takes a signal to travel from the Initiator to the Responder and back to the Initiator. We then subtract the known processing time in the Responder and divide this by 2, resulting in only the ToF propagation time in one direction. To determine the distance between the two devices, the ToF is multiplied by the speed of light.
Because the UWB signal is so distinct and easy to receive, even in multipath environments, it is easier to identify, with a high degree of certainty, exactly when pulses depart and arrive. UWB can accurately track pulses at an exceptionally high rate of repetition, so it is possible to make fine-grained ToF calculations even at very close range within 10 cm.
Wi-Fi and Bluetooth standards also attempt to measure distance, but results so far limit the accuracy of ToF calculations to between one and five meters. Another factor that reduces the accuracy of Wi-Fi and Bluetooth readings is their performance in multipath environments. The multipath components of modulated sine waves, which create inaccurate timing events when measuring ToF, can only be separated in a complex manner, and this makes it very difficult to deliver measurements more precise than one meter.
It is important to note that ToF calculations by themselves determine distance, not direction. Yet ToF diagrams are typically drawn in the shape of a circle because the UWB response signal also contains angle of arrival (AoA) information. With the proper antenna setup and calculations, AoA can determine a very accurate position on that circle, the angle at which the target device is located. At each antenna in the AoA array, there is a small but discernible difference in the arrival time, as a measured phase of each pulse is received. The arrival time and phase of each signal is noted and then used in a geometric calculation, similar to triangulation, through which the angle of the received signal can be accurately determined. This presents a noteworthy benefit over Wi-Fi and Bluetooth that could also work with a sectorized antenna array, but lacking certain temporal elements and operating at the longer wavelength 2.4GHz ISM band would produce much less accurate results.
PROTECTING TOF CALCULATIONS
The original UWB standard for ranging, 802.15.4a, which was released more than a decade ago, did not emphasize security the way it probably would if it were released today. As a result, ToF calculations based on the 802.15.4a version can be vulnerable to distance manipulations.
If a person can interfere with the timestamps or other aspects of the ToF calculation, then he or she can alter the proximity calculations. This is a serious issue with secure access applications, including hands-free access control, where tricking the system into thinking that an authorized user is close by when they are not can trigger a lock to open when it shouldn’t.
In testing the 4a standard, researchers found that an attacker could decrease the measured distance of a UWB ToF calculation by as much as 140 meters with a probability higher than 99 percent. The vulnerability has to do with the IEEE 802.15.4a version of the physical layer, or PHY. Concern about this vulnerability is part of what prompted the development of a revised UWB standard, called IEEE 802.15.4z, which is nearing completion.
BOOSTING SECURITY FOR ULTRA-WIDEBAND
The IEEE 802.15.4z HRP UWB PHY adds a scrambled time stamp (STS) field into the packet. The idea is to keep ToF-related data from being either accessible or predictable by adding cryptographic keys and number randomness to the PHY packet. This helps to combat various external attacks, including those mentioned above, which use the deterministic and predictable nature of the original UWB PHY to manipulate distance readings. The updated approach offers the best possible protection against brute force attacks, which also aim to manipulate distance measurements.
The STS field consists of a set of pseudo-random binary phase shift keying (BPSK) modulated pulses. The pseudo-randomness of the BPSK modulation sequence is ensured by a cryptographically secure pseudo-random number generator. Due to the pseudo-randomness of the sequence, there is no periodicity, thus allowing reliable, highly accurate and artifact-free channel delay estimates to be produced by the receiver.
For efficient decoding of the STS, the receiver needs to have a copy of the sequence locally available before the start of reception. Meeting this requirement is a responsibility that falls to higher-layer STS seed management. This management is now within the scope of other industry organizations that are building on top of the IEEE specification.
The IEEE 802.15.4z amendment adds PHY-level protection to all known attacks on legacy UWB radios and makes UWB much more robust from a security standpoint and far less vulnerable to attack.
A PROMISING FUTURE
As a technology with nearly 60 years of history behind it, UWB is poised for its next stage of growth. At present, UWB is the only commercially available wireless technology that delivers highly accurate and highly precise location and fine ranging measurements while also supporting high-level security to protect access credentials and data communications.
UWB’s unique combination of signal characteristics – easy to identify, resistant to noise and reflection, separate from other signals – makes it an excellent choice for measuring distance, and its support for high-level security makes it ideally suited for secure access applications and location-based services.
UWB is not new, but in its present form, as a secure fine ranging technology, it has found new relevance. UWB’s unique combination of precision and protection is likely to become the basis for secure access and location services of all kinds. In particular, UWB shows promise for secure transactions in mobile devices by driving the convergence of hands-free access, location-based services, payments, identification, and device-to-device interactions.
About the author: This email address is being protected from spambots. You need JavaScript enabled to view it. is vice president, business development, for HID Global. She is also the Marketing Working Group co-chair for the FiRa Consortium.